The Philippines BSP Circular No. 1213 introduces specific changes that will reshape authentication policies across financial institutions in the Philippines, with a one-year compliance window starting June 2025. The pressing question now is how to adapt effectively
Bangko Sentral ng Pilipinas (BSP) Circular No. 1213, issued in June 2025, is a regulation mandating stricter, phishing-resistant, device-bound authentication for financial institutions in the Philippines to combat digital fraud. The circular aims to enhance security in digital customer onboarding, transactions, and session management by replacing insecure methods like SMS/email OTPs with stronger tools such as passkeys and biometrics.
The requirements apply to all BSP-supervised financial entities, including banks, fintech companies, payment providers, and lending firms, and cover critical areas such as:
- Digital onboarding and customer login processes
- Authorization of transactions
- Device and session management
- Ongoing identity proofing
Financial institutions have one year from June 2025 to fully comply with all the requirements of this Circular.
1. Specific regulations
BSP Circular No. 1213 highlights the growing security risks of traditional OTP methods – particularly those delivered via SMS or email—and advises against their use. This stance reflects global recognition that such channels are highly vulnerable to phishing, SIM swap attacks, and other forms of social engineering.
Biometric authentication, Behavioral biometrics, Passwordless authentication (biometrics, hardware tokens and cryptographic keys, FIDO), Adaptive authentication, considered perfectly aligned with BSP Circular No. 1213 because they directly address the circular’s core security objectives: preventing phishing, eliminating interceptable authentication, and binding user access to a secure device.
Fundamentally, the provisions of BSP Circular No. 1213 adopt a similar approach to those of other countries around the world, as cyberattacks are a global issue.
2. Comprehensive Compliance Solution – SAM Auth Server
With over 20 years of experience in developing encryption, identity, and authentication solutions, Savyint offers one of the most comprehensive authentication platforms, fully meeting and even exceeding the requirements of BSP Circular No. 1213.
SAM Auth Server is an all-in-one strong authentication solution that enables system authentication, data encryption, transaction encryption, multi-layer authentication, multi-level security, and integration with hardware security devices as well as software functional modules, ensuring maximum safety for electronic transactions.
2.1 Key features of the solution
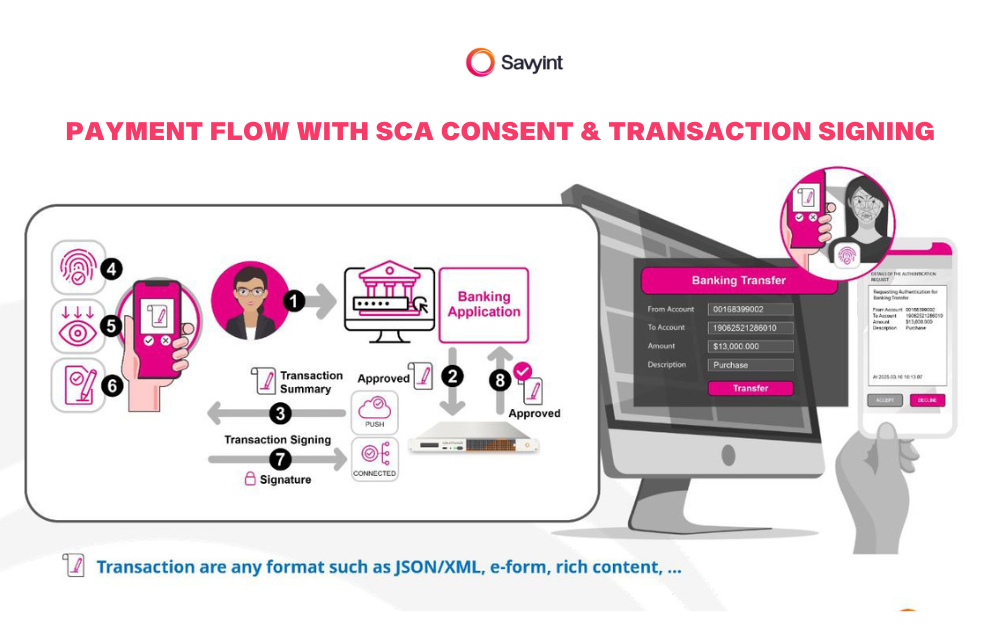
Transaction Authentication Features
- Transaction Signing: Contextual authentication codes linked to transaction details
- Push Authentication: Authentication requests sent via push network
- WYSIWYS (What You See Is What You Sign): Displays a transaction summary for the user to review and confirm
- Independent Channel/Connection Authentication: Transaction signatures are sent directly from the mobile app to the server
- Flexible Activation Model: Token activation via self-service in the mobile banking app when using the Mobile SDK, or via email/SMS OTP, or biometric verification matching the customer’s data when using the TrustSign Mobile App
- RASP Features: Protection against code cloning, source code protection, PIN protection, runtime integrity checks
Access Control
- PIN/Biometric Access: Authentication using the user’s PIN or biometrics (facial recognition, fingerprint) on the device
- Weak PIN Detection: Alerts and prevents weak PIN setup during TrustSign Mobile App/SDK activation
- Token Blocking: Token locked after several consecutive incorrect PIN entries
- Biometric Login Blocking: Triggered when biometric data on the device is altered
Token Types
- OTP Tokens: Use TOTP/OCRA algorithms to generate one-time passwords — TOTP1, TOTP2, OCRA Challenge Response, OCRA Transaction Signing
- PKI Tokens: Use standard Public Key Infrastructure (PKI) with asymmetric key pairs and X.509 certificates for mobile devices
Data Encryption – Transaction Encryption
Encrypt data and transactions, ensuring that all information cannot be stolen or tampered with during initiation, storage, and transmission.
Integration with AML monitoring systems and Fraud Management Systems (FMS)
2.2 Full compliance with international standards
- FIPS 140-2 level 2 & level 3 security certifications
- NIST AAL2 /AAL3, FIDO2/Passkey
- ISO/IEC 29115 LoA3/ LoA4, eIDAS Substantial/High
- ISO 9001:2015, ISO 14001:2015 and ISO 27701:2022 CSC 1.0, CSC 2.0 compliant and Rest API Service Interface
- SCA PSD2/eIDAS compliance and CC EAL4+ AVA_VAN.5 certification and ALC_FLR.2 certificate for EN 419 221-5 security standard
- Compliance standards: GDPR, SOC 2 Type II, HIPAA & PCI DSS
- Comply with the Payment Services Directive (PSD2/PSD3) for customer authentication
- Comply with Philippines BSP Circular No. 1213
With a flexible design and high scalability, SAM Auth Server can be easily deployed across various system models (on-premise, cloud), supports multiple platforms, and delivers the most advanced authentication methods available today.
Contact us now for a consultation HERE!







