of surveyed organizations expressed concern about the threat of “harvest-now, decrypt-later” attacks
Source: Capgemini Research Institute
of banking websites currently support PQC
Source: F5
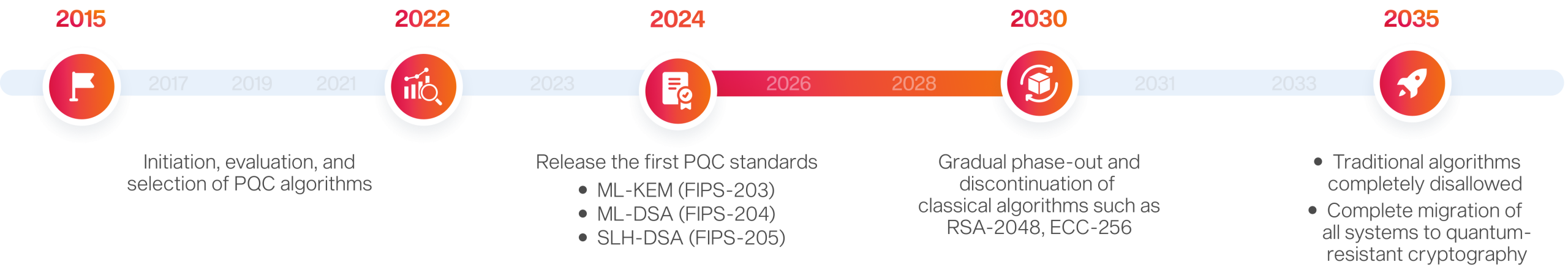
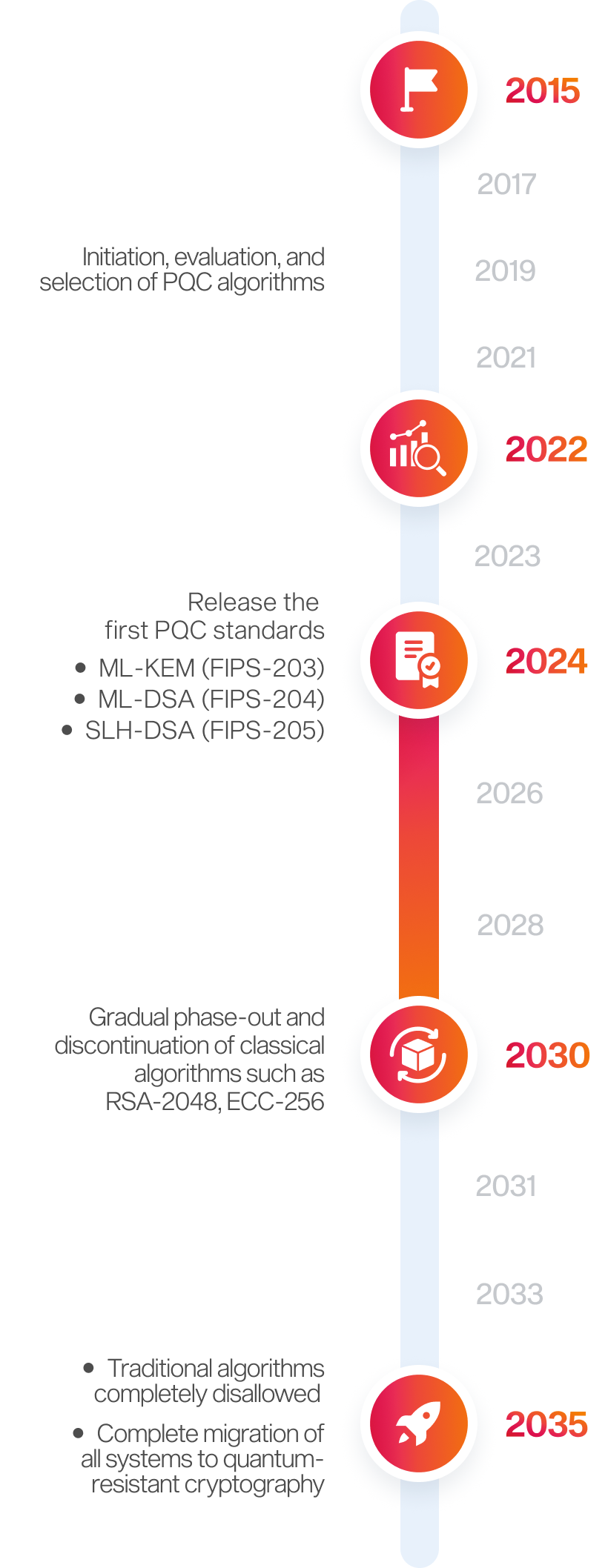
is the milestone in NIST’s roadmap to begin phasing out classical cryptographic algorithms (RSA-2048 and ECC-256)
Source: U.S. National Institute of Standards and Technology (NIST)

Savyint PQC Lab
Vietnam’s first dedicated Post-Quantum Cryptography (PQC) Lab, building solutions to safeguard the digital future

Utilize HSMs that support NIST-standardized PQC algorithms
Issue and automate the provisioning of PQC digital certificates

Administer the full lifecycle of digital certificates and consolidate certificates requiring migration
Provide a flexible and secure sandbox environment for rapid testing, isolated from live production systems
Benefits of PQC

Long-term data protection
Prevents “Harvest Now, Decrypt Later” attacks by protecting sensitive data for decades to come

Future-proof security
Resistant against both classical and quantum computer attacks

Global standard compliance
Aligns with NIST PQC standards to meet international security requirements

Securing critical systems
Ensures safety for PKI, digital signatures, IoT, and blockchain against quantum threats

Enhanced trust & business advantage
Builds customer trust, enhances global competitiveness, and positions organizations as security leaders
How does PQC work?

Lattice-based Cryptography
Leverages the difficulty of solving complex structured mathematical problems called lattices—algorithms considered highly resistant even to powerful quantum computers

Hash-based Cryptography
Utilizes cryptographic hash functions to generate digital signatures, offering resilience against quantum computing-based attacks
Multivariate Polynomial Cryptography
Employs systems of multivariate quadratic equations. The mathematical complexity of these equations makes the method robust against quantum cryptanalysis

Code-based Cryptography
Harnesses error-correcting codes to provide a reliable foundation for post-quantum secure encryption

Isogeny-based Cryptography
Uses isogenies on elliptic curves to design quantum-secure cryptographic systems, ensuring strong and resilient protection against future quantum threats
NIST PQC Timeline & Transition Roadmap
Benefits of PQC
Use cases

Finance
Quantum-safe payments and transactions; deployment of public key infrastructure (PKI) and post-quantum digital certificates

Government
Securing e-IDs, eGovernment services, and citizen data

Network & Telecommunications Infrastructure
Securing communication channels and telecom networks against quantum attacks

Industry & Defense
Enhancing security for industrial systems, defense, and national security

Smart Cities & IoT
Quantum-safe authentication for billions of devices






















