Key Functions of the Validation Authority Service
- Very easy to install and configure without any special training requirements – just follow the product quick guide
- One installation of VA Server can support multiple complex trust models and respond for multiple CAs, each with a unique validation policy
- Security for operations staff is vital – this is provided using secure web-browser management screens with detailed role-based access controls to system functions plus optional feature selectable dual control management
- Provides advanced CRL handling options - CRL streaming for efficient import of very large CRLs, indirect CRLs, flexible CRL polling, multiple CRL source monitoring and an option to use real-time certificate status data from CAs
- Provides an option to use real-time certificate status information for white list checking to ensure that a certificate was actually issued by the target CA
- High-availability CRL watchdog feature, where multiple VA Server instances work in an automated master / slave relationship
- Configurable e-mail based alert system for system administrators
- Full certificate path building and verification logic for OCSP requestors, CAs and peer OCSP responders
- Provides detailed event and transactional reporting for effective management
- Automated human-readable conversion of detailed OCSP transaction messages for effective debug analysis of reported trust issues or interoperability checking
- Detailed, tamper-resistant logs which record all activity and OCSP transactions for dispute resolution with full reporting or filter capabilities
- Auto-archival of old transaction records
- Implements concept of “cross-validation” for linking disparate PKIs together through validation rather than cross-certification
- Supports unique “manual routing” of OCSP messages for interoperability with 1st Generation PKI (which contain no OCSP address information)
- Supports RSA to 8912-bit, ECDSA to 521 bits, SHA-2 and SHA-3 algorithms
- Support for Entrust HSM, Thales HSMs, Utimaco HSMs and other PKCS#11 compliant HSMs
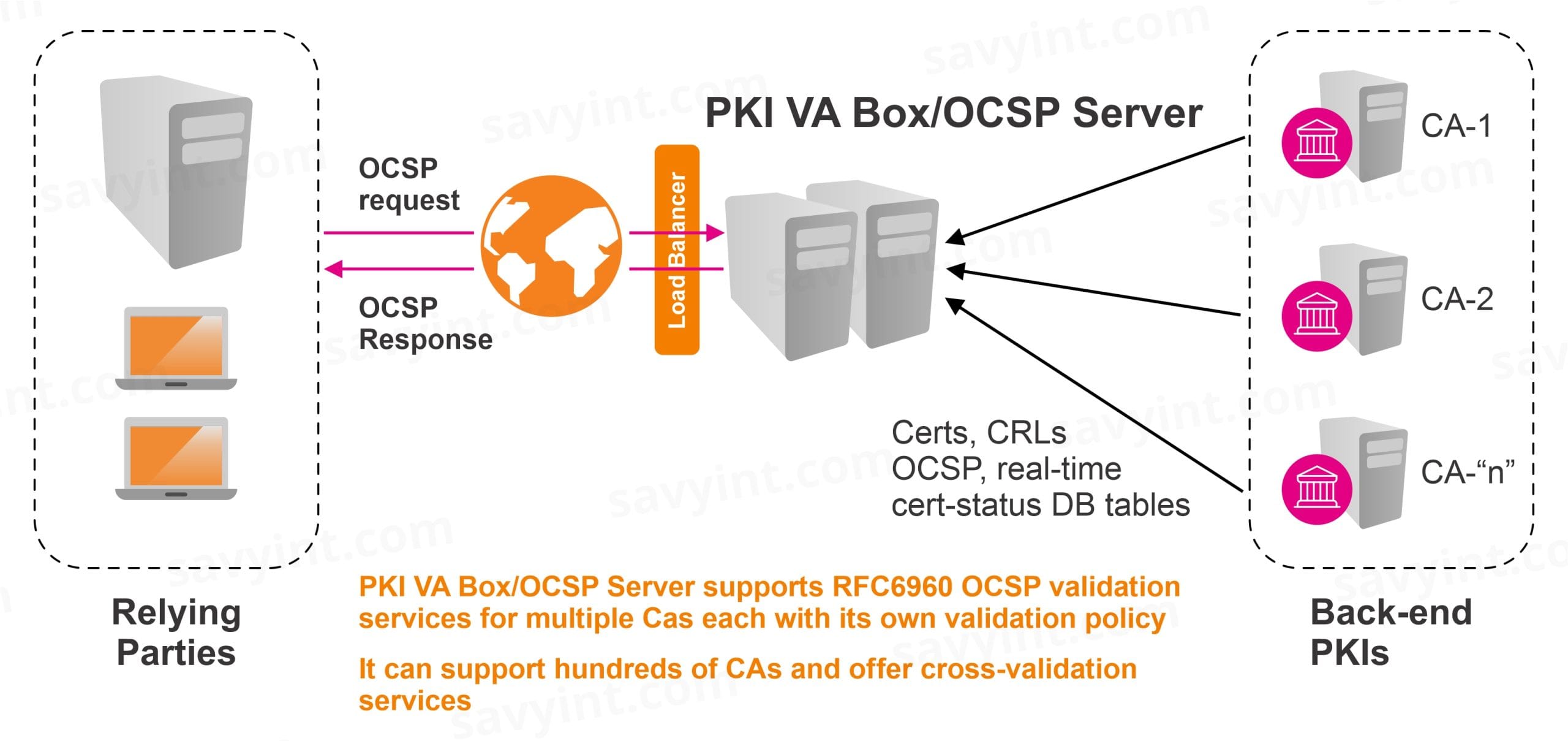
A single instance of VA Server can respond for an unlimited number of CAs (limited only by the capacity of the server and the license purchased).
An example of such a configuration is already being operated as part of a PKI existing used EJBCA software, where VA Server is being used as a central point of VA gateway for validation services on behalf of all of the recognized CAs whose certificates are accepted for access to e-Gov services.
The benefits of using a VA hub solution for many CAs can again be measured in terms of reduction in software/hardware costs plus it acts as a single point of reference for all management reporting, resolving support issues and performing centralised configuration. To the outside world it will appear as if a dedicated OCSP responder is servicing each CA.
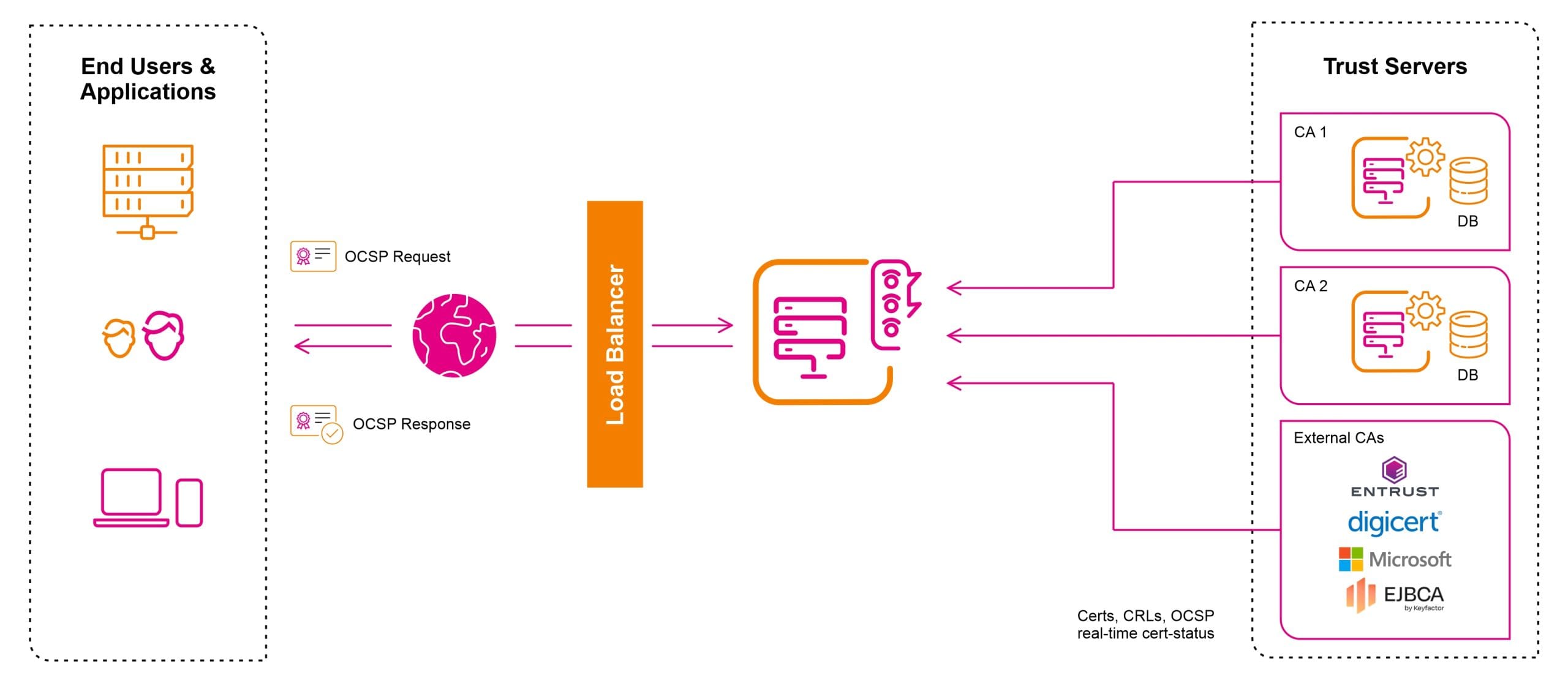
A VA System with consolidate database & real-time status certificates with single-point CDP/AIA URL.
VA Server manages each CA separately; this includes the use of separate keys and certificates when responding on behalf of each CA. The validation policy covers the following points:
- Each CA can enforce its own trust model on how the VA Server OCSP response signing keys should be certified (e.g. self-signed or delegated).
- Each CA can define its own method for CRL retrieval (e.g. HTTP/S or LDAP/S) and precise repository locations (multiple online repositories can be defined for failover purposes).
- CRL Management is very advanced and defines how often the CRLs should be retrieved and what happens if a CRL failure is seen is also configurable on a per CA basis. CRL Freshness is a configurable check so that CAs that over-issued CRLs can be monitored to confirm this is being done.
- How OCSP forwarding to peer OCSP responders should work and how the verification of peer OCSP responders should be managed is fully configurable on a per CA basis.
- The VA Server administrator can also define unique certificate quality levels (explained further below) for each CA. This information can be returned in a private OCSP extension to provide value-add information about the certificate rather than just its revocation status.
High Performance
The performance of an VA OCSP responder depends on many factors including whether or not VA OCSP transactions are being conducted over SSL/TLS, whether requests are signed and hence require authentication by the server, size of VA OCSP responder keys, number of certificates being checked within a single request, size of CRLs, whether an HSM is being used, the specification of the OCSP responder and database machines etc.
VA Server has been optimised for high performance use in large PKIs, although speed is actually a secondary goal to the primary task of providing effective logging of system events and transactions.
PKI VA Server using VA gateway Agent Utility (RPU) retrieves these individual certificate revocation files from any a CA and publishes the new updated revocation information they contain to a real-time certificate status database. VA Server utilises this to over-ride the last CRL information with AD/LDAP and thus provide real-time certificate status information within the OCSP Service such as below:
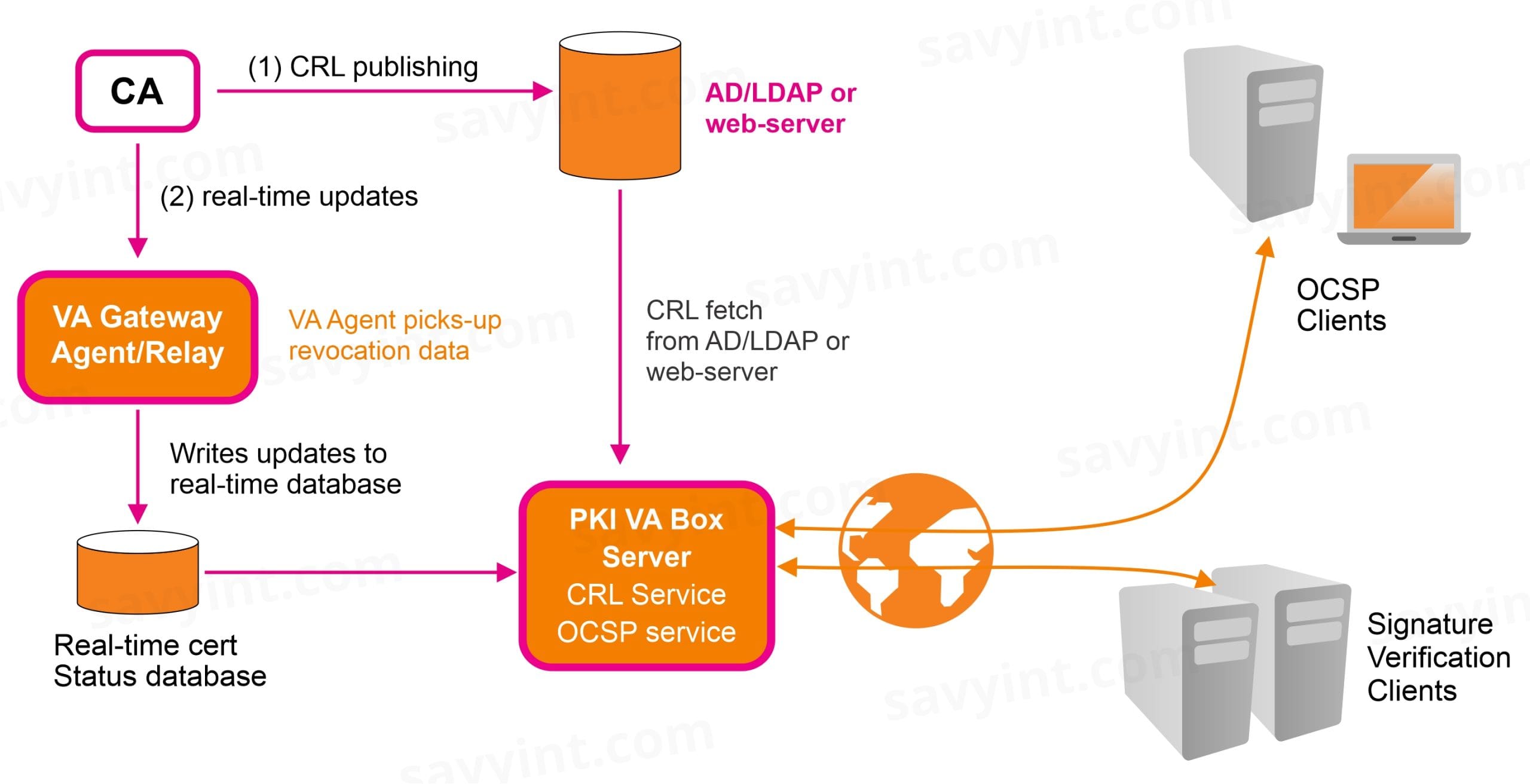
We provider a VA Solution with full certificate Status Checking means checking a certificate’s revocation status, plus a check to ensure that it was actually issued by the identified CA. To achieve this VA OCSP Server needs to have real-time access to the full set of certificate status information maintained by the registered CAs within Trust Manager. Real-time checking of CRLs alone cannot satisfy the whitelist checking requirement because they only contain the details of revoked certificates.
To deliver real-time full certificate status checking VA OCSP Server needs to access a database of up-to-date certificate status information as illustrated below:
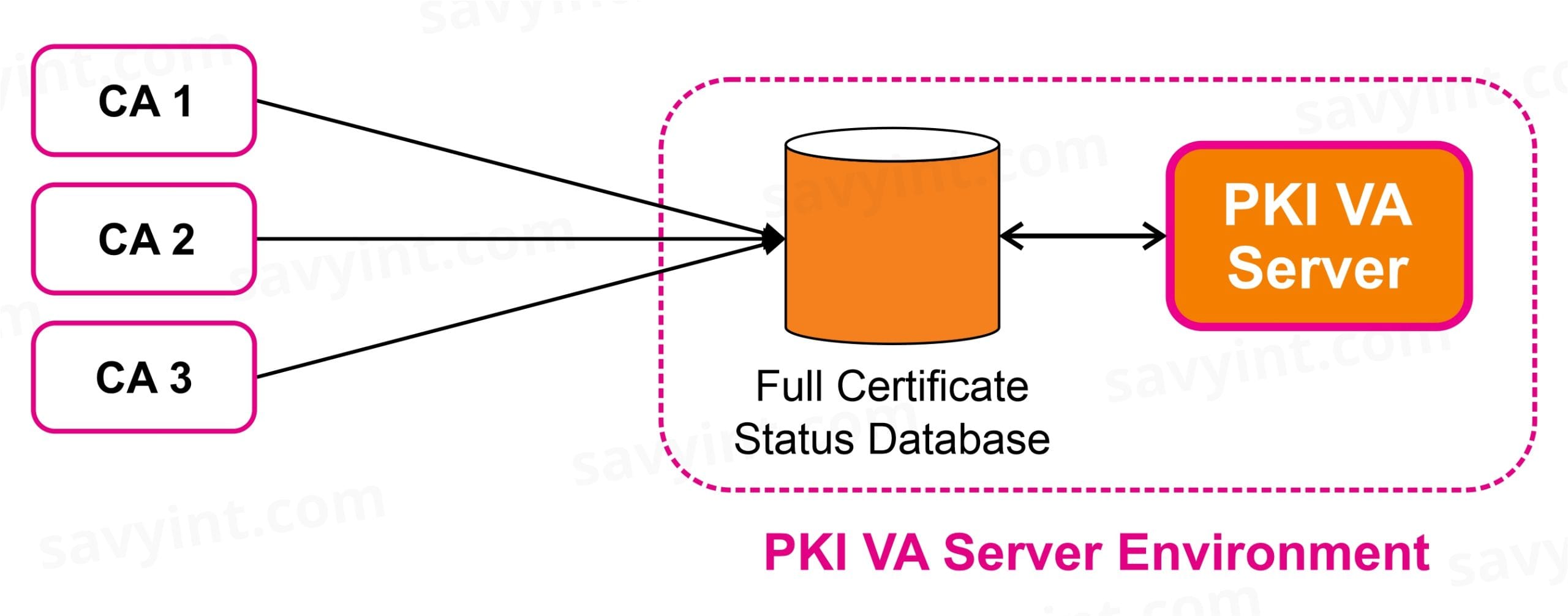
The Full Certificate Status Database is managed outside VA Server box and is quite separate to the standard VA Server database that contains configuration data, transaction records and other information.
The URL Certificate Status Database option can be used with multiple CAs. Each CA is responsible for populating and updating its certificate status table, or a separate application must do this.
